Successfully monitoring Linux file access is a very important milestone for users or Linux administrators confined in a shared or public network setting. Linux file access monitoring helps us answer questions like Who has had access to this file within the last week? Can I get a username list of all users accessing file x? Can I know when file y is being accessed?
The set logging policies on your Linux operating system distribution should give us timely statistics regarding the system user and the period in which queried file(s) were accessed.
Auditd or Audit Daemon emulates a Linux Auditing System solely focused on the userspace component. Under the Linux operating system spectrum, anything that is labeled a daemon implies that it is a background running service/application. Therefore, Auditd comfortably runs as a background service while collecting and writing audit-associated log files.
Auditd Features
By installing and using Auditd on your Linux operating system distribution, you will be able to meet/implement the following audit-related functionalities:
- Log of incoming and outgoing, from and to, system information.
- Log of authenticated user events e.g. ssh.
- Log of audit configuration files changes.
- Log of timestamp and even information e.g. event type and outcome.
- Log of sensitive files or database changes e.g. /etc/passwd file’s passwords.
- Log of audit log files access attempt.
- Log of triggered events and users responsible for it.
Install Auditd (Linux Auditing System)
Before we look at the installation steps needed to have auditd up and running on your Linux operating system distribution, make sure you meet the following requirements/prerequisites:
- You have sudoer/root user privileges on your Linux system.
- You are comfortable with using the Linux command-line environment.
Reference the following auditd installation commands in regards to the Linux OS distribution you are using:
$ sudo apt install audit [On Debian, Ubuntu and Mint] $ sudo yum install audit [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-process/audit [On Gentoo Linux] $ sudo pacman -S audit [On Arch Linux] $ sudo zypper install audit [On OpenSUSE]
Auditd (Linux Auditing System) Usage
We are now ready to configure and manage auditd for tracking security-related information on our Linux systems.
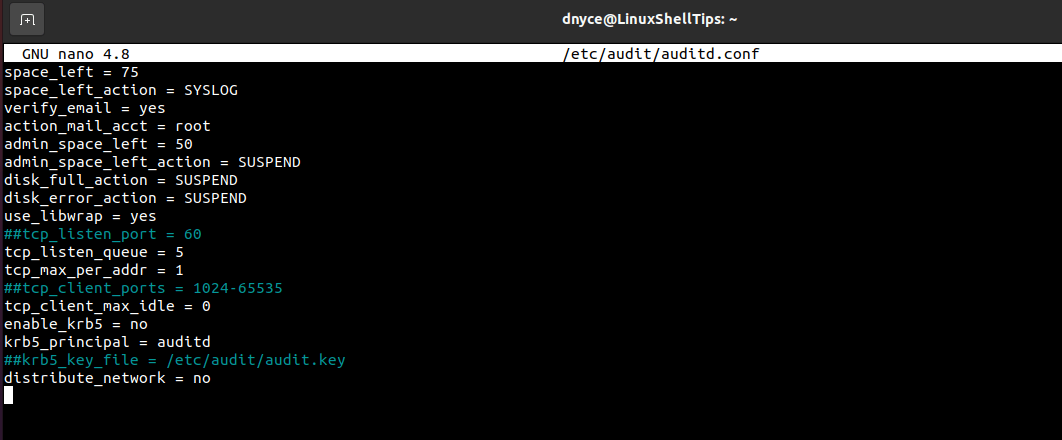
The file path /etc/audit/auditd.conf points to the main audit configuration file. Accessing the auditd.conf file requires sudoer/root user privileges.
$ sudo nano /etc/audit/auditd.conf
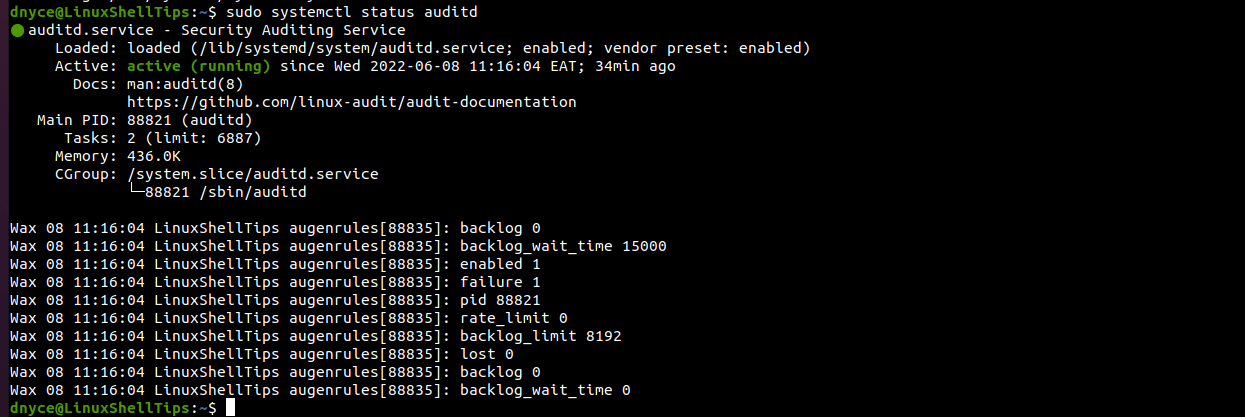
To start, enable and verify the status of auditd, we’ll use the service command in place of the systemctl command for user ID (UID) accuracy.
$ sudo service auditd start $ sudo systemctl enable auditd $ sudo systemctl status auditd
Defining Audit Rules in Linux
We’ll need to use the auditctl tool to add system call-related auditing rules. For instance, we can define a watch rule which monitors file access types like read, write, execute, or even check for attribute changes.
The watch rules syntax is as follows:
# auditctl -w path_to_target_file -p permissions -k key_name
Example 1: Audit on User Creation Actions
Watch (-w) the /etc/passwd file for changes associated with a write (w) and attribute (a) as set permissions (-p). Key name (-k) helps us uniquely identify the created watch rule.
$ sudo auditctl -w /etc/passwd -p wa -k user-modify
Stored logs related to auditd can be found in the file /var/log/audit/audit.log.
Let us create a Linux user to see if auditd will log the changes.
$ sudo useradd new_user
Time to check the auditd log file:
$ sudo cat /var/log/audit/audit.log | grep user-modify
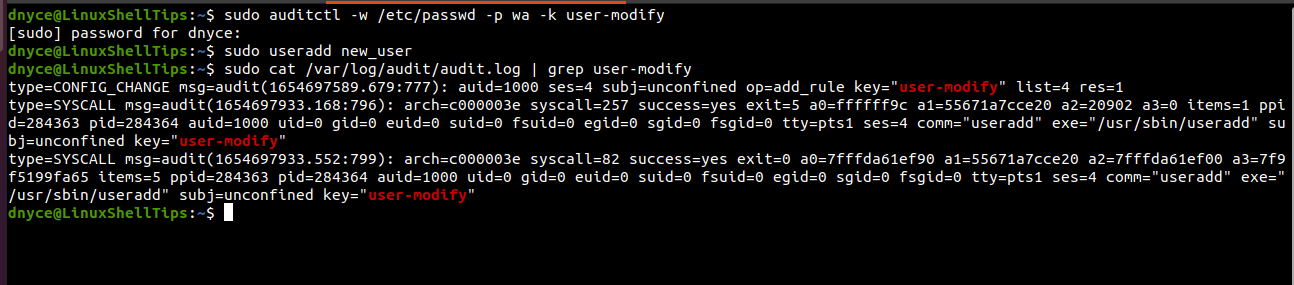
The above output has some rich information like the type of command executed if the command was executed successfully, user id (uid), group id (gid), and process id (pid) used in the creation of new_user.
Example 2: Audit User actions on Directory X
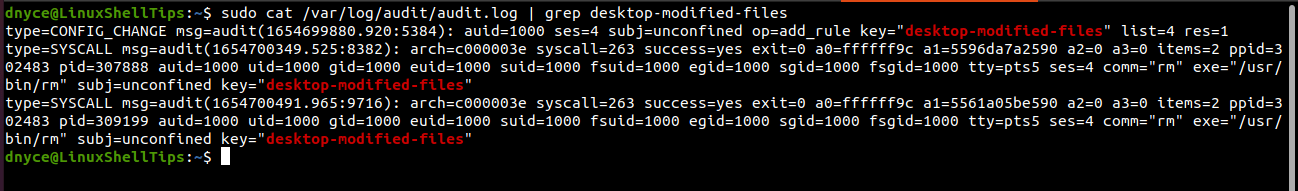
The below command monitors read, write, execute, and attribute (rwxa) permissions on desktop files.
$ sudo auditctl -w /home/dnyce/Desktop -p rwxa -k desktop-modified-files
Perform some read, write, execute, and attribute (rwxa) actions on your desktop environment.
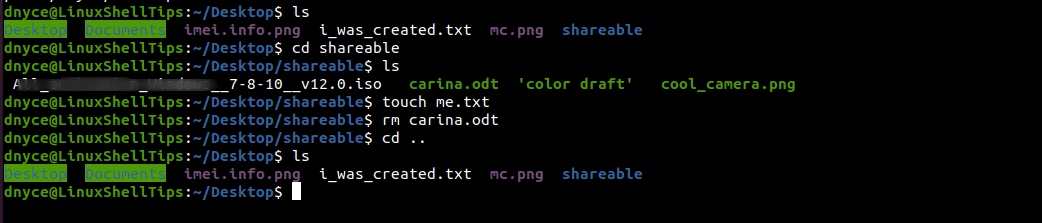
and check if the auditd updated its log file.
Persistent Audit Rules in Linux
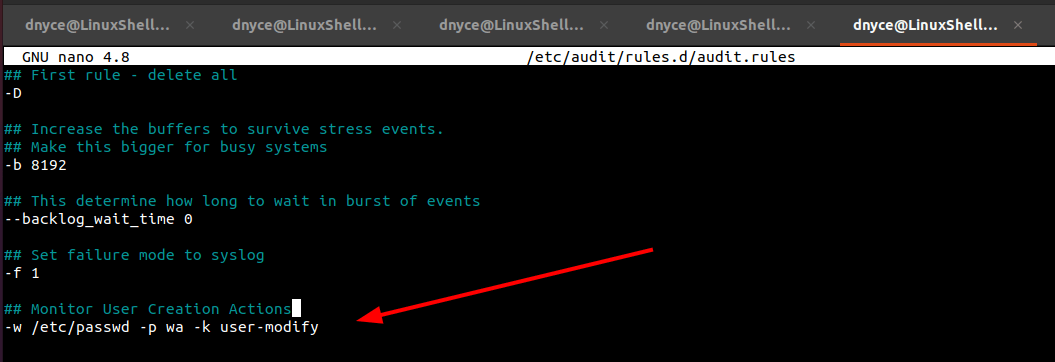
These are watch rules (without auditctl) that persist even after the system reboot. For instance, to make the audit on user creation actions persistent, we’ll open the following file.
$ sudo nano /etc/audit/rules.d/audit.rules
and save the watch rule:
-w /etc/passwd -p wa -k user-modify
Finally, reload the audit daemon.
$ sudo service auditd reload
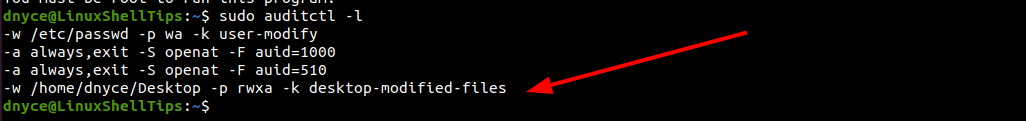
Confirm the audit rule addition by listing it:
$ sudo auditctl -l
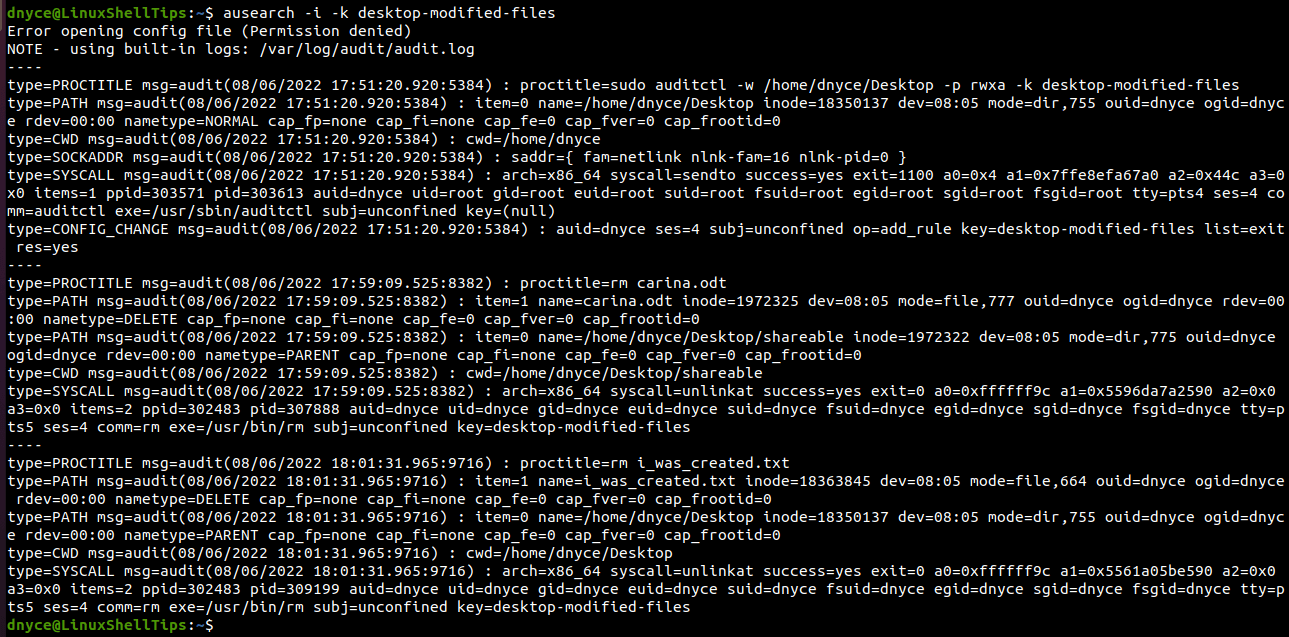
Searching Audit Logs in Linux
We can search audit logs by pointing to their key names:
$ ausearch -i -k desktop-modified-files
Creating Audit Reports in Linux
The generated reports can point to executable (-x) events.
$ sudo aureport -x
We now understand how easy it is to monitor Linux File Access actions both temporarily and persistently via the Auditd utility.
